"Hi, I need your phone number for an urgent task," or "Download the following file to check your progression report." Do these phrases sound familiar to you? You're not alone! According to Statista, there were 480,000 cyberattacks in the United States in 2022, and that number is only growing every year.
Cybercriminals are lurking around the corner every hour of the day, attacking computer systems, stealing data, or extorting companies with ransomware. As a result, cybersecurity and crime are one of the hottest topics of 2024 for companies, trying to protect their data, clients, and employees.
What are the biggest cyberattacks in 2024, and how can you, as a company, protect yourself from these attacks? This article will give you answers to all these questions.
The Evolution of Cyberattacks and Cybersecurity
Cybersecurity is the result of a long evolution and multiple cyberattacks. We have shortened that history to the basics, based on the article of Cybercrime Magazine:
1940’s
As the internet evolved, including advancements like the cloud, Gmail, and social media, so did cybercrime, becoming more precise and organised. After the invention of the digital computer in 1943, access to computer systems was limited to only a few people, as many did not understand the processes involved. At that time, hackers primarily sought unauthorised access without specific financial, political, or economic goals.
1950’s
Surprisingly, financial cyberattacks didn’t originate with computer systems, but rather with cell phones. In the late 1950s, a new type of cybercrime emerged: 'phone phreaking.' 'Phreaks' were individuals who could manipulate protocols, allowing for cost-free calls and bypassing long-distance fees.
1960’s
The sixties marked an interest in hacking, but it still lacked any economic or political goals. The hackers were mostly curious students who sought to gain access to companies’ systems for fun. The advantage for companies was that they could investigate their digital vulnerabilities. In 1967, IBM even invited some students to attempt hacking their systems, which subsequently led to the implementation of more defensive measures.
1970’s
Computer hacking actually began in 1972 with the computer program ‘Creeper,’ which left a breadcrumb trail saying, ‘I’m the creeper, catch me if you can.’ In response to the computer worm ARPANET developed 'Reaper', aiming to remove the computer worm. This program marked the birth of cybersecurity. Governments and companies started to realise that hacking would become a significant problem, leading to increased attention to cybersecurity worldwide.
1980’s
In the 1980s, more high-profile attacks were executed on organisations, such as National CSS. It's no surprise that in 1987, the first commercial antivirus was introduced to our world.
1990’s
The 90s were a thriving time for both antivirus developers and hackers, as they battled each other for digital dominance. While many companies offered antivirus solutions, hackers also created their own anti-antivirus programs. Towards the end of the decade, a new problem emerged: email, which became a playground for viruses, such as the Melissa Virus.
2000’s
The year 2000 marked the real onset of cyber threats as more homes and companies integrated the internet and digital devices. It was no longer necessary to download an infected file; merely clicking on an infected website was enough.
Cybersecurity rapidly evolved with antivirus software adding new features such as anti-malware and operating system security. Additionally, antivirus solutions became available for Android and Windows mobile platforms.
2010-2024
The next generation of cyberattacks began in 2010, with a focus on national security that cost countries millions. Cybercriminals have since evolved into highly orchestrated and stealthy operations, utilising advanced techniques such as ransomware-as-a-service and supply chain compromise. The proliferation of interconnected devices through the Internet of Things (IoT) has expanded the attack surface, providing adversaries with new vectors to exploit.
Furthermore, the commodification of hacking tools and the emergence of nation-state-sponsored cyber warfare have heightened the stakes, blurring the lines between criminal enterprises and geopolitical conflicts. As organisations increasingly rely on digital infrastructure to conduct business, cyberattacks have evolved from isolated incidents to systemic threats capable of causing widespread disruption, financial losses, and reputational damage.
Companies must therefore continually adapt their cybersecurity posture, leveraging proactive defence strategies and cutting-edge technologies to effectively mitigate the evolving threat landscape. Examples of modern cybersecurity measures include multi-factor authentication, real-time data monitoring, cloud security, and zero-trust architecture.
The Biggest Cyberattacks of 2024
The history of cyberattacks teaches us that cybercriminals continually try to innovate their tactics and devices to attack businesses. But what are the most common cyberattacks of 2024?
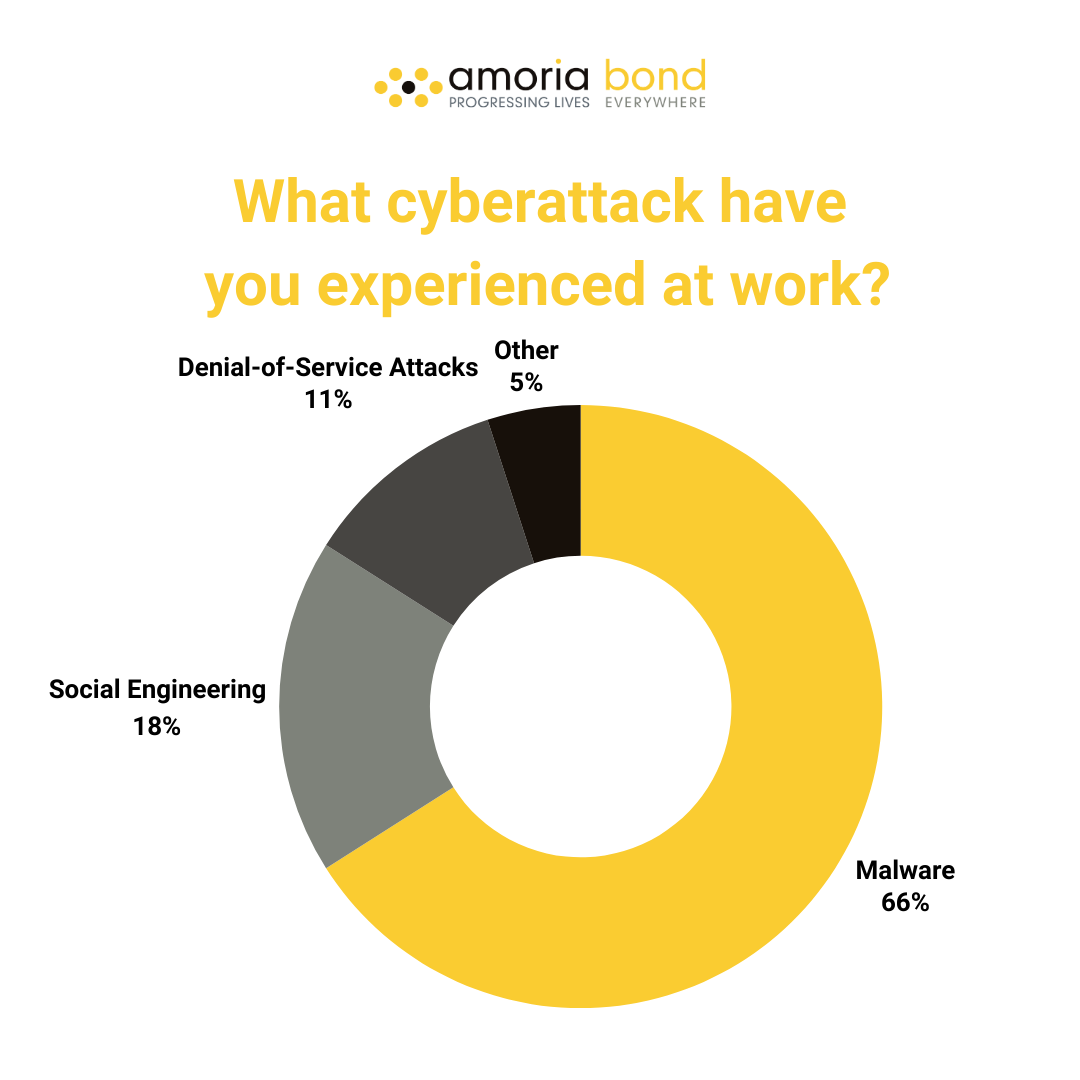
We launched a poll on LinkedIn, which asked our followers what cyberattack they have experienced at work. In total, 38 people responded.
The biggest threat according to our followers is malware, with 66%. Social engineering and Denial-of Service Attacks got respectively 18% and 11%. Only 5 of the respondents indicated that they experience other cyberattacks.
Social Engineering
Social engineering is a form of psychological manipulation used to deceive individuals or groups into sharing confidential information, performing actions, or making decisions that they normally wouldn't. It’s the most common cyberattack with over 500 million phishing attacks reported in 2022.
This tactic exploits human behaviour rather than hacking complex systems, often relying on techniques such as persuasion, manipulation, and impersonation. Social engineers may use various mediums including phone calls, emails, or face-to-face interactions to achieve their objectives. Common social engineering attacks include phishing, pretexting, baiting, and tailgating. The goal of social engineering is typically to gain unauthorised access to information, systems, or resources, making it a significant threat to individuals, organisations, and even entire societies.
How can you protect your company from social engineering? Firstly, it’s crucial to educate your staff on cybersecurity. Provide cyber awareness training to ensure your employees are less vulnerable to phishing emails or malicious websites. Secondly, implement multi-factor authentication to enhance the security of your systems and prevent unauthorised access by hackers. Lastly, install antivirus software to prevent employees from downloading suspicious files or clicking on fraudulent websites.
Malware
Malware, short for malicious software, refers to any software intentionally designed to cause damage, disrupt operations, or gain unauthorised access to computer systems, networks, or devices. Malware has a wide range of malicious programs, including viruses, worms, Trojans, ransomware, spyware, and adware, each with its own method of infiltration and malicious intent.
Malware can be distributed through email attachments, infected websites, removable media, or software vulnerabilities. Once installed on a system, malware can steal sensitive information, encrypt files for ransom, disrupt system functionality, or turn the infected device into a bot for further cyberattacks.
Mitigating the risks of malware requires a multi-layered approach, including using antivirus software, regularly updating systems and software, exercising caution when downloading or clicking on links, and implementing robust security measures to detect and respond to malware threats effectively.
Europol has recognised the severity of malware and has disrupted the criminal operation of the LockBit ransomware group at every level, severely damaging their capability and credibility. LockBit is widely recognised as the world’s most prolific and harmful ransomware, causing billions of euros worth of damage.
Denial-of-Service Attacks
A denial-of-service (DoS) attack is a malicious attempt to disrupt the normal functioning of a targeted server, service, or network by overwhelming it with a flood of illegitimate traffic. These attacks aim to render the targeted system inaccessible to its intended users, thereby causing disruption or downtime. Attackers typically exploit vulnerabilities in network protocols or application layers to orchestrate massive volumes of traffic, exhausting the target's resources such as bandwidth, processing power, or memory.
In recent years, Distributed Denial of Service (DDoS) attacks, which involve multiple compromised devices coordinated to launch an attack simultaneously, have become increasingly prevalent and sophisticated. The motivations behind DoS attacks vary, ranging from financial gain through extortion to ideological or political agendas.
Defending against DoS attacks requires robust network security measures, including intrusion detection and prevention systems, traffic filtering, and rate limiting, as well as close monitoring and rapid response capabilities to mitigate the impact of such attacks.
Other Cyberattacks
5% of our respondents indicated that they have experienced other cyberattacks than the ones mentioned above. We have listed other possible cyberattacks below:
1. Man-in-the-Middle (MitM): Attackers intercept and potentially alter communication between two parties, allowing them to eavesdrop on sensitive information or manipulate it maliciously.
2. SQL Injection: Attackers insert malicious SQL code into web application input fields, gaining unauthorised access to databases, retrieving sensitive data, or altering/deleting information.
3. Cross-Site Scripting (XSS): Attackers inject malicious scripts into web pages, stealing cookies, session tokens, or other sensitive data, and redirecting users to malicious sites or performing unauthorised actions.
4. Brute Force Attacks: Attackers systematically try all possible password or encryption key combinations to gain unauthorised access to a system.
5. DNS Spoofing/Cache Poisoning: Attackers manipulate the Domain Name System (DNS) to redirect users to malicious sites or intercept their communication, facilitating phishing, malware distribution, or data theft.
6. Insider Threats: Individuals within an organisation misuse their access privileges to steal data, sabotage systems, or engage in other malicious activities.
7. Advanced Persistent Threats (APTs): Highly skilled adversaries conduct targeted attacks with specific objectives such as espionage, sabotage, or financial gain, often going undetected for long periods.
8. Cryptojacking: Attackers secretly use victims' computing resources to mine cryptocurrency, typically by infecting systems with malware or exploiting web application/browser vulnerabilities.
Partnering with a Cybersecurity Recruitment Organisation
The number of successful cyberattacks on banks doubled in the period 2018-2020 in the Netherlands. The Netherlands are sadly not the only country with poor cybersecurity. In their neighbouring country Germany, only 2% of companies are ready for cyberattacks, which is a decrease of 9% percent in comparison to 2023. That’s an odd evolution, considering that in the last 12 months 55% of German companies received a cyberattack.
The cybersecurity market is growing steadily every year, which means that the talent pool is getting scarcer. At the same time, cybercriminals evolve their tactics to attack companies. That’s why companies need cybersecurity experts, who can safeguard optimise cybersecurity measures.
Working with a cybersecurity recruitment organisation can provide invaluable support and expertise to companies seeking to protect their digital assets and safeguard against cyber threats. Cybersecurity staffing organisations recruit professionals with specialised knowledge and experience in identifying vulnerabilities, assessing risks, and implementing effective security measures tailored to the unique needs of each client.
Progress Your Life with Amoria Bond
At Amoria Bond every consultant wants to progress the lives of our clients, candidates, and the wider community. That’s why our teams devote themselves every day to find your company the best cybersecurity specialist possible. We have access to a global talent pool, which means that we always find the perfect fit for your vacancy. Our 360° solutions offer tailored services to clients, meeting their budget, deadline and demands. Contact us for more information about our award-winning services or if you are a cybersecurity expert, upload your cv to find your next exciting job!






